http://www.javamex.com/tutorials/cryptography/ciphers.shtml
Comparison of ciphers
Java supports a number of encryption algorithms out of the box. Which encryption algorithm to use can depend on a number of criteria:
- how secure the algorithm is currently judged to be in the cryptographic literature;
- the performance characteristics of the algorithm (e.g. the "raw speed" of the algorithm, and whether it supports parallel encryption);
- how politically safe a decision it is to use a particular algorithm (paradoxically, this doesn't necessarily depend directly on the algorithm's security);
- whether you have to interact with a legacy system.
Summary of algorithms
We compare measured speed of encryption with various algorithms available as standard in Sun's JDK, and then give a summary of various other characteristics of those algorithms. The encryption algorithms we consider here are AES (with 128 and 256-bit keys), DES, Triple DES, RC4 (with a 256-bit key) and Blowfish (with a 256-bit key).
Performance
First, the easy bit. Figure 1 shows the time taken to encrypt various numbers of 16-byte blocks of data using the algorithms mentioned.
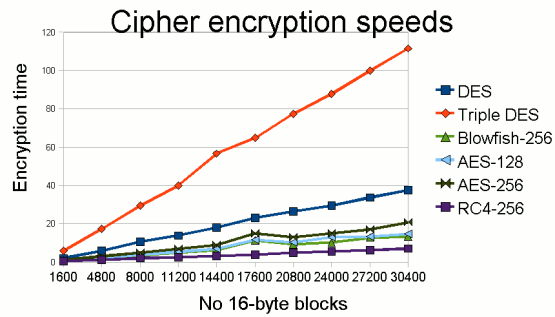
Figure 1: Comparison of encryption times for various common
symmetric encryption algorithms provided as standard in Java 6.
It's important to note right from the beginning that beyond some ridiculous point, it's not worth sacrificing speed for security. However, the measurements will still help us make certain decisions.
Characteristics
Table 1 gives a summary of the main features of each encryption algorithm, with what I believe is a fair overview of the algorithm's current security status.
| Algorithm | Key size(s) | Speed | Speed depends on key size? | Security / comments |
| RC4 | 40-1024 | Very fast | No | Of questionable security; may be secure for moderate numbers of encrypted sessions of moderate length. RC4 has the redeeming feature of being fast. However, it has various weaknesses in the random number sequence that it uses: see Klein (2008)1. |
| Blowfish | 128-448 | Fast | No | Believed secure, but with less attempted cryptanalysis than other algorithms. Attempts to cryptanalyse Blowfish soon after publication are promising (Schneier, 19952 & 19963). But, unlike AES, it doesn't appear to have received much attention recently in the cryptographic literature. Blowfish has been superseded by Twofish, but the latter is not supported as standard in Java (at least, not in Sun's JDK). |
| AES | 128, 192, 256 | Fast | Yes | Secure, though with some reservations from the crypto community. It has the advantage of allowing a 256-bit key size, which should protect against certain future attacks (collision attacks and potential quantum computing algorithms) that would have 264 complexity with a 128-bit key and could become viable in the lifetime of your data. |
| DES | 56 | Slow | – | Insecure: A $10,000 Copacobana machine can find a DES key in an average of a week, as (probably) could a botnet with thousands of machines. The simple answer is: "Don't use it– it's not safe". (RFC 4772). |
| Triple DES | 112/168, but equivalent security of 80/112 | Very slow | No | Moderately secure, especially for small data sizes. The 168-bit variant estimated by NIST (2006) to keep data secure until 20304. Triple DES performs three DES operations (encrypt-decrypt-encrypt), using either two or three different keys. The 168-bit (three-key) variant of Triple DES is generally considered to offer "112 bits of security", due to a so-called meet-in-the-middle attack. AES offers a higher level of security for lower CPU cost. |
Remarks on AES
AES stands for Advanced Encryption Standard and is actually an algorithm that was originally called Rijndael, after its inventors Rijmen & Daemen. It is the algorithm that most people will end up using unless they have a strong reason to use anything else:
- it is a politically safe decision: the encryption standard of the US National Institute of Standards and Technology (NIST), and the US government reportedly approves AES with 192 or 256-bit keys for encrypting top secret documents (or put another way, your boss won't sack you for choosing AES...);
- it is largely considered secure, though with some reservations:
- nobody yet has (publicly) a full attack on AES, or a partial attack that is practical (though some impractical partial attacks exist5);
- however, AES is algebraically simpler than other block ciphers: effectively, it can be written as a series of mathematical equations, and there is a worry that somebody could demonstrate a way to solve those equations (see Ferguson & Schneier, Practical Cryptography, pp. 57-58);
- the NSA may have chosen Rijndael as they secretly know how to break it, or secretly estimated that they could develop a way to break it.
- it is fast (Ferguson & Schneier (op cit), p. 59, argue that this is the reason it was picked over Serpent as the AES standard).
Key sizes
On the next page, we look at the issue of choosing and setting key sizes for encryption in Java.
'아키텍쳐 ' 카테고리의 다른 글
| Technical Debt (2) | 2013.10.30 |
|---|---|
| License Key Management (0) | 2013.08.01 |
| API platform (0) | 2013.07.17 |
| API design for client which support limited HTTP method (0) | 2013.07.10 |
| 아키텍트의 종류와 역할 (3) | 2012.09.06 |